Medical device security is no longer a “back burner” issue — it’s critical. In this article, we’ll explore emerging industry cybersecurity issues, regulations, and the important steps you can take to secure and manage your medical devices from current and future threats.
According to Deloitte, medical devices have increasingly been the target of cyberattacks. Because these devices provide critical services, cybercriminals think healthcare companies will quickly pay a ransom. This uptick in medical device cyber incidents has disrupted supply chains, manufacturing processes and research that resulted in hundreds of millions in damages and reputation. At the same time, the pandemic accelerated medical IoT adoption to reduce in-person contact. In fact, IoT medical devices will almost quadruple in value by 2027.
What Is Medical Device Security?

Simply stated, medical device security requires device developers to not only integrate security best practices into their device designs, but also to ensure that those devices can be monitored and updated to keep them secure over their lifecycle.
Medical device security is possibly the most urgent security issue facing the healthcare industry currently. Medical device OEMs must utilize security tools and processes to prevent unauthorized access to or control of those devices and their associated data. And they must build in the capability to remotely send out firmware security updates reliably as threats emerge.
Why Cybersecurity Is Important for Medical Devices

Because diagnostic medical devices such as MRI machines, CT scanners, and X-ray machines increasingly connect to networks, they’re vulnerable to the same hacking, malware, and ransomware attacks as other types of networked hardware.
According to some estimates, 20-30 billion medical devices in the U.S. are connected in the growing Internet of Things (IoT) landscape. These IoT medical devices include infusion pumps, insulin pumps, pacemakers, medical wearables and even ventilators. According to a Moody’s report, an IT security company reported an almost 10,000 percent increase in attempted attacks on healthcare customers between 2019 and 2020.
In the case of these medical devices, an attack can compromise a patient’s private data or even their health. Recent ransomware attacks resulted in patient deaths when an Alabama hospital was unable to use fetal heartbeat monitors after the devices had been hacked. That’s why the Food and Drug Administration (FDA) has established guidelines and requirements for connected medical devices security. Compliance with these regulations falls to manufacturers as well as healthcare providers.
Who Is Responsible for Medical Device Security?

In the United States, the Food and Drug Administration regulates medical devices and one of the FDA’s top cybersecurity priorities is the threat of ransomware on medical devices. However, medical device cybersecurity is the responsibility of both connected device manufacturers and suppliers as well as the healthcare organizations that use them, underlining that there may be security breaches anywhere in the medical environment.
How Do You Secure A Medical Device?

Medical device manufacturers and healthcare organizations form the first line of defense in reducing cyberattacks on their devices. By incorporating some defensive measures and proactive monitoring, medical device manufacturers and healthcare associates can enhance the security of their devices while safeguarding the well-being of patients using their devices.
The issues with cyber security medical devices face is increasing over time, which makes these considerations imperative at every phase of the chain from development to end use. Here are some steps medical device manufacturers can take.
- Build security into the medical device from the start. When cyberattacks become public, governing agencies such as the FDA name the manufacturer and product involved. That kind of publicity can ruin customer and end user trust. That’s why elevating security as a core feature or intrinsic property right in the design phase of a device makes sense and becomes mandatory.
- Identify potential threats and vulnerabilities and build a plan. Perform a medical device security risk assessment to identify potential threats medical devices face and build a risk management plan for addressing these risks, of course, keeping it updated relentlessly.
- Establish strong authentication. Build in robust authentication mechanisms to limit access to critical functions and sensitive data.
- Employ encryption and data protection techniques. Encryption can protect sensitive data when applying best practices for data storage and transmission.
- Establish a patch management and vulnerability monitoring process. Consider remote management systems that help centrally and remotely monitor and update security patches and firmware.
Resources
Emerging Medical Device Security Regulations

By the end of 2020, the healthcare industry paid around $20.8 billion in downtime — almost double 2019 amounts. In fact, the number of records affected in 2020 increased by 470 percent since 2019. Even worse, healthcare providers paid around $2.1 million in ransom for patient data.
FDA Cybersecurity Guidelines
Then in early in 2023, the FDA began requiring medical devices to meet specific cybersecurity guidelines which were written into law. To address growing medical device security vulnerabilities from cyberattacks on hospitals and internet-connected devices, all new medical device applicants now must share their plans for monitoring, identifying and managing cybersecurity issues. This is a major change from how medical device manufacturers must address the safety and security of their products from their conception, throughout their lifetime, until obsolete.
The new FDA medical device security requirement includes:
- A documented process for assuring that medical devices are adequately protected.
- Deploy security updates and patches on a regular schedule and in critical situations.
- Share a software bill of materials (SBOM) that includes all open-source and other device software, including commercial packages.
Additionally, the FDA now plans to refresh its medical device cybersecurity guidance every two years.
European Union Medical Device Cybersecurity Guidelines
In Europe, MDR 2017/745 and IVDR 2017/746 cover the newest medical devices. The documents outline new essential safety and security requirements for all medical devices with programmable systems, as well as software medical devices.
The NIS2 Directive and GDPR legislative acts include the cyber security standards for medical devices and for managing personal patient data. Finally, the EU Cybersecurity Act includes a cybersecurity certification framework that promises to strengthen IT processes, products and services protections.
International Medical Device Cybersecurity Guidance Documents
Internationally, two guidance documents outline basic cybersecurity principles for the life of the medical devices. First, the International Medical Device Regulators Forum drafted the Principles and Practices for Medical Device Cybersecurity. Then, the Medical Device Coordination Group published the EU MDCG 2019-16 Rev.1 Guidance on Cybersecurity for Medical Devices.
Emerging Trends in IoT Medical Device Security

Because regulators hold medical device vendors accountable for security, interest in finding new ways to reduce medical device cybersecurity threats is growing. Keep an eye on these emerging technology trends:
- Artificial intelligence (AI) and machine learning (ML) — Artificial intelligence can help healthcare IT teams bucket data and select the most cost-effective security strategies rather than apply a one-size-fits-all approach to data security.
- Blockchain technology — Blockchain technology can store an unintelligible, uneditable, decentralized and transparent log of all patient data and can conceal sensitive patient data such as a person’s identity. Because blockchain is decentralized, it also allows patients and healthcare providers to share the same information quickly and safely, without jeopardizing the custody of patient data.
- Zero trust architecture — The core idea behind zero trust architecture is “never trust, always verify” that treats every connection on the network as a potential threat. Instead of the traditional approach of authenticating once and trusting for the remainder of the session, this approach minimizes security breaches risks by granting access on a need-to-know basis.
- Microsegmentation — By dividing a network into smaller segments or zones, network administrators can reduce the risk of unauthorized access. By using microsegmentation, healthcare providers can limit an attacker’s movement in the network and keep ransomware attacks from interfering with medical devices.
Learn how Digi TrustFence enables OEMs to integrate device security, device identity, and data privacy capabilities.
Take the Next Steps in Securing Your Medical Devices
 There is no doubt that medical device security standards are important and will become increasingly so in the coming years. That’s why healthcare providers and medical device manufacturers alike should prioritize security as IoT medical device growth and demand grows.
There is no doubt that medical device security standards are important and will become increasingly so in the coming years. That’s why healthcare providers and medical device manufacturers alike should prioritize security as IoT medical device growth and demand grows.
To start, select a seasoned wireless and wired communication partner with deep expertise in IoT device security who understands medical device security best practices. That’s where Digi can help. Since 1985, Digi has been a pioneer in wireless and wired communications and provides end-to-end solutions across industries.
The Digi ConnectCore ecosystem is a complete suite of embedded modules, software, tools, and services. The ConnectCore platform provides connected solutions in highly regulated industries such as industrial and energy, medical, EV charging and banking where security is crucial.
A key component, our highly integrated system-on-modules, have unique benefits, including:
- Industrial reliability — Designed to last for at least 10 years, have a 24/7/365 duty rating for continuous use and come with a default 3-year product warranty.
- Deep integration — Digi SOMs seamlessly integrate with the XBee® ecosystem, Wi-Fi, and Bluetooth protocols. They also support IoT standards such as LTE cellular, mesh networking and long-range sub-GHz wireless connectivity.
- Industry leading security — All Digi SOMs incorporate the Digi TrustFence IoT security framework and a hardware Secure Element (SE).
- Flexible connectivity — A range of connectivity options make Digi SOMs suitable for a wide variety of applications.
- Scalable portfolio — As your application evolves, developers can simply drop in a higher performance, compatible, Digi ConnectCore module.
- Engineering services — Digi Wireless Design Services can augment your developer team at any point along the way, from prototyping to developing, testing, certification and manufacturing readiness services.
- Best-in-class support — From complete documentation to a host of integrated tools and technical support services, Digi ensures you have everything you need for development and deployment success.
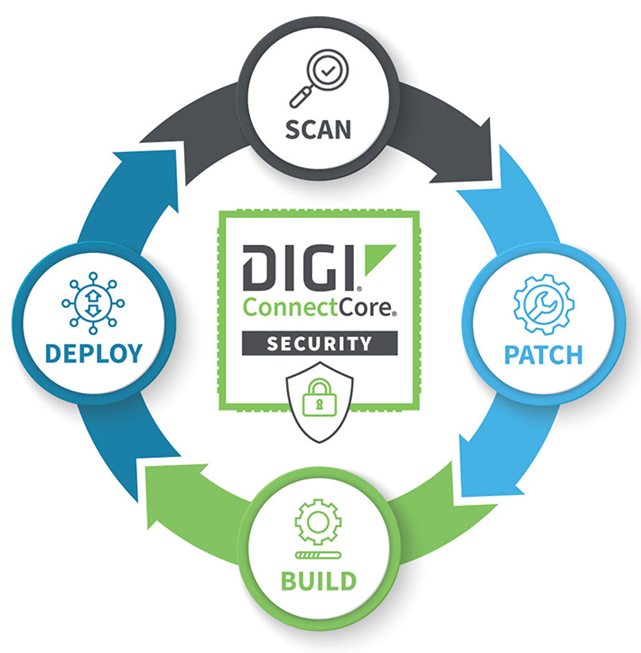
- Digi ConnectCore Security Services and Digi ConnectCore Cloud Services provide the capabilities you need to scan and monitor devices for new and evolving security threats, and remotely and securely manage field-deployed devices over their full lifecycle.
Let us help you with your medical device IoT security so you can confidently continue improving the health of your patients.
Next Steps