A digital signature is a widely used security technique for assuring the integrity of data and authentication of its signer.
The first step in creating a digital signature is to use asymmetric cryptography (also known as public-key cryptography) to generate a pair of keys:
-
Public key: available to anyone. It is used during the authentication process.
-
Private key: only known by the signer. It is used in the signing process.
These keys are complementary: if data is encrypted with the private key, then the public key is required to decrypt the data. In a similar way, if the public key is used to encrypt the data, the private key should be used in the decryption.
To generate the signature of a document, encrypt it with the private key, which only the signer has. Note that this does not provide any confidentiality: the public key is known by anyone, so anyone can decrypt the document. However, decrypting the signature with the public signer key and obtaining the same document guarantees that:
-
The signature was generated by the private key. (Otherwise, the decryption procedure would fail.) Since only the signer has access to the private key, the signature was generated by the signer.
-
The document has not been modified. (Otherwise, the document would not match the one obtained from the signature.)
Since the signature is the same size as the document, the signed document ends up being twice the document size. To solve this problem, a cryptographic hash is introduced.
A cryptographic hash (also know as digest) is a function that maps data of any size to data of a fixed size and which is designed to be a one-way function. This means that given the hash of some data, it should be extremely computationally difficult to deduce the data from which that hash was generated. Several properties of the hash allows the function to be used in this context without introducing weakness in the scheme:
-
Changes in the data produce changes in the hash of the data in an untraceable way.
-
Given the hash of some data, it is infeasible to generate other data that has the same hash.
Instead of encrypting the entire document to generate the signature, the signature is generated from just the hash of the document. This generates a very small signature that is independent of the size of the data being signed. The image below shows the complete process:
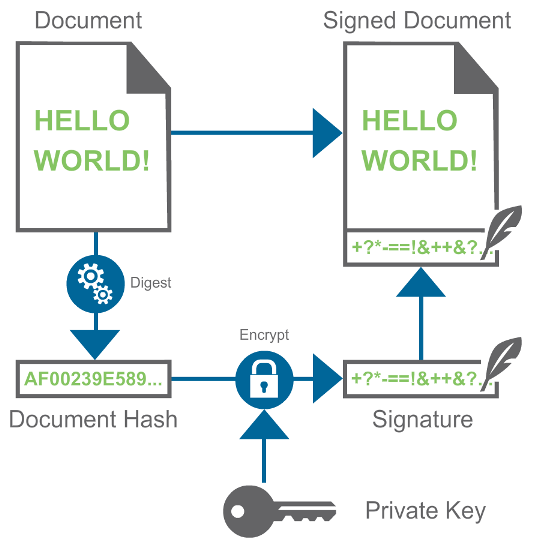
Authenticating a signed document
To authenticate a signed document, follow this procedure:
-
Decrypt the signature to obtain the hash of the original document.
-
Compute the hash of the document.
-
Compare the hashes. For them to match, the following conditions must be met:
-
The document has not been modified. This provides the integrity guarantee.
-
The key that was used to generate the signature is the private key associated to the public key that you used. This provides the authentication guarantee.
-
If the hashes match, the signature is correct and the document is valid. The following diagram illustrates the authentication process:
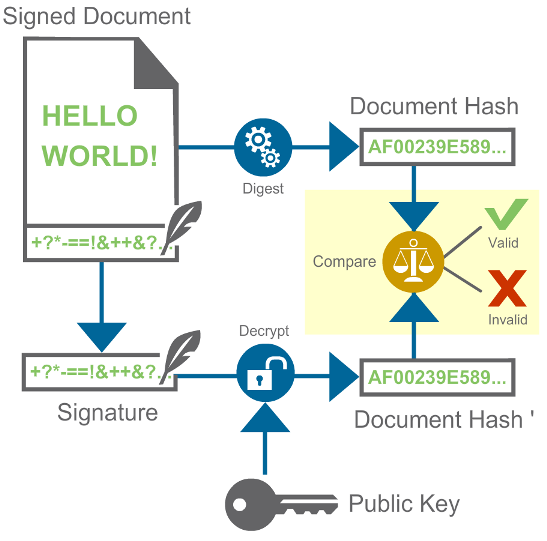
How can you be sure that the public key is the signer’s public key? If an attacker provides a public key as if it were the public key that the signer used, the attacker could use their private key to sign images. There are several ways to solve this problem.
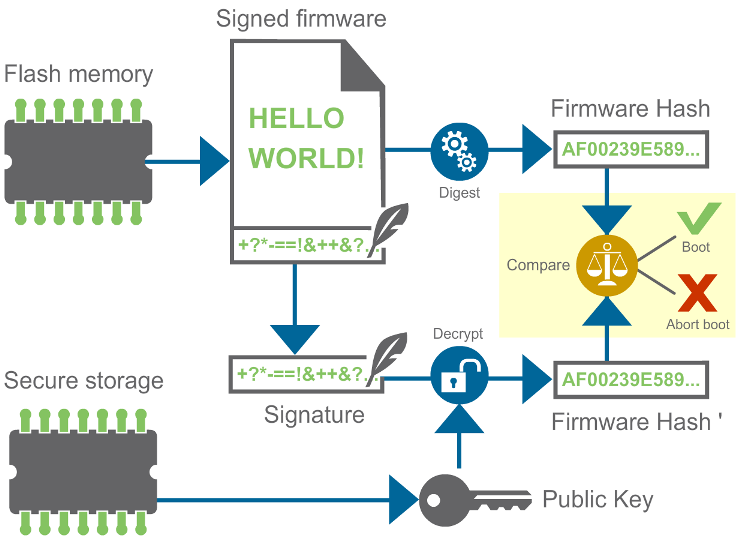
Validating and booting signed firmware
For firmware validation, the most common approach is to program the public key in the device’s secure storage memory during manufacturing. The secure storage guarantees that the public key cannot be altered and was programmed by the signer. This scheme for validating and booting signed firmware images is shown below: