The Open Portable Trusted Execution Environment (OP-TEE) is a mini operating system that facilitates the communication between the secure and the normal worlds.
Secure world vs normal world
The Arm TrustZone architecture splits resources in two different execution environments:
-
the secure world: TF-A, OP-TEE
-
the normal world (non-secure): U-Boot, Linux
The concept of the two worlds extends beyond the processor to encompass memory, software, bus transactions, interrupts, and peripherals within an SoC.
The basic rules between the worlds are:
-
The secure world can access any resource from the normal world.
-
The normal world cannot access any resource from the secure world.
Components
Secure world |
|
|---|---|
OP-TEE core |
A secure privileged layer, executed in Arm Cortex-A secure state |
TEE trusted libraries |
A set of secure user space libraries designed for Trusted Applications (TA) |
Normal world |
|
OP-TEE Linux driver |
Linux TEE framework and driver ( |
TEE client API |
A user space library that allows user space applications to communicate with Trusted Applications (TA) running in the secure world. |
TEE supplicant |
A Linux daemon ( |
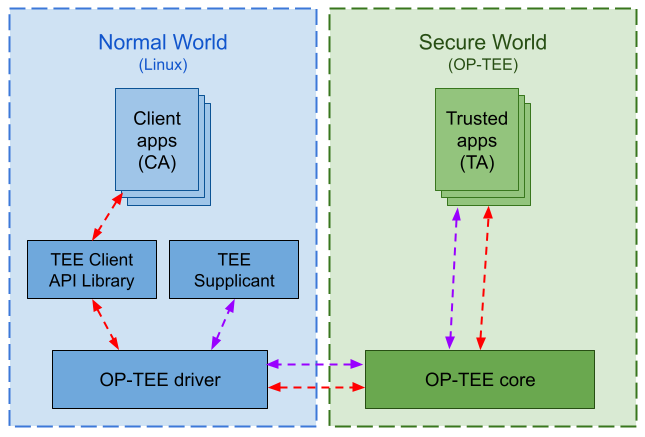
Workflow
The following diagram represents the communication flow between the normal and the secure worlds:
Source code
The source code for ConnectCore MP15 OP-TEE OS is available at https://github.com/digi-embedded/optee_os/tree/3.16.0/stm/maint.
This is forked from the SoC vendor (STMicroelectronics) repo, which is itself a fork of the original repo, hosted by Linaro. This repo contains the SoC customizations by STMicroelectronics as well as Digi customizations for the SOM.
Current supported version is 3.16.0.
Device tree configuration
The OP-TEE can manage its configuration with a device tree. This device tree includes the hardware required for the OP-TEE to work and defines the security rules to access secure peripherals from the normal world (U-Boot, Linux).
The device tree for the ConnectCore MP15 is available at https://github.com/digi-embedded/optee_os/blob/3.16.0/stm/maint/core/arch/arm/dts/ccmp15-dvk.dts
Digi Embedded Yocto recipe
The recipe that builds the OP-TEE is called optee-os-stm32mp and belongs to meta-st-stm32mp layer.
The OP-TEE OS is merged with U-Boot in the tf-a-stm32mp recipe, which produces a Firmware Image Program (FIP) binary called fip-ccmp15-dvk-optee.bin.
To build the FIP binary from within a Digi Embedded Yocto project:
$ bitbake tf-a-stm32mpRead more
You can read more on OP-TEE OS implementation for the STM32MP15 at https://wiki.st.com/stm32mpu/wiki/OP-TEE_overview




