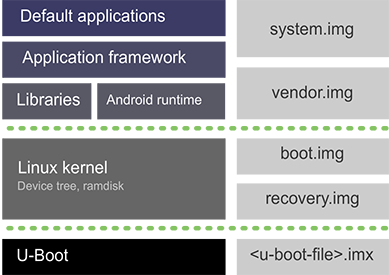
Android is architected in the form of a software stack comprising applications, an operating system, run-time environment, middleware, services, and libraries. All these layers can be simplified in this form:
-
Android applications: The top of the stack is where all the built-in applications, third-party applications, and your own applications live. Digi provides a set of sample applications demonstrating the new APIs.
-
Application framework: The second layer includes the application framework, which gives you the tools to write applications such as the SDK, activity managers, location managers, notification managers, and the view system. This level includes the set of new built-in Digi API extensions to access new hardware interfaces: I2C, SPI, CAN, ADC, GPIO, CPU and GPU management, Ethernet, PWM, serial port, and watchdog.
-
Libraries and Android runtime: The hardware access layer is where libraries are located for interacting with Ethernet, Wi-Fi, Bluetooth, and other hardware features. The runtime is also at this layer. Each application runs in its own virtual machine (VM) instance, which means that applications cannot directly invade each other’s process space. The system provides Linux-style permission controls while maintaining an open system through Intents and other interprocess communication capabilities.
-
Linux kernel: At its lowest level, the Linux kernel handles drivers, power management, and other low level processes.
-
U-Boot: Residing below all these layers, U-Boot is not part of Android, but it is needed to load the Android components.
Build artifacts
When the Digi Embedded for Android platform is built, it generates the following build artifacts (files):

-
system.img: This is the Android operating system image. It includes all the Android libraries, runtimes, API frameworks, and default applications that run in the device.
-
vendor.img: The vendor partition contains any binary that is not distributable to the Android Open Source Project (AOSP). It holds all the proprietary binaries or any other vendor specific files.
-
boot.img: This image includes the kernel, the ramdisk, and the device tree configuration. U-Boot executes this image after boot, and it mounts the rest of the Android partitions.
-
recovery.img: This image is very similar to the boot.img. It also includes the kernel, a ramdisk, and a device tree configuration to boot in recovery mode. U-Boot only executes this image if the recovery boot mode is requested, usually to install update packages or wipe data and cache partitions.
-
<u-boot-file>.imx: This file contains the U-Boot bootloader. This is the first piece of code that is executed when the device boots. It initializes the device and launches the operating system.
eMMC layout
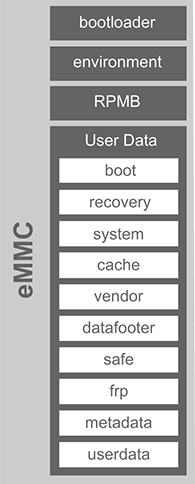
The eMMC (internal memory of the ConnectCore 8X device) is split into four physical partitions:
-
bootloader: This partition contains the U-Boot bootloader image that is executed when the device is powered on. It starts the installed operating system and allows some device configurations.
-
environment: This partition contains the U-Boot environment and its redundant copy.
-
RPMB: This is the replay-protected memory-block partition, used to manage data in an authenticated and replay-protected manner. It is not currently in use.
-
User Data: User Data holds the operating system divided into the following logical partitions:
-
boot: This partition contains Android’s kernel, ramdisk, and one or more device tree configurations. This is the partition where the boot.img file is programmed.
-
recovery: This partition contains an Android kernel, ramdisk, and the device tree configurations for the recovery boot mode. This is the partition where the recovery.img file is programmed.
-
system: This partition contains the entire Android operating system, other than the kernel and the ramdisk. This includes the Android user interface as well as all the system applications that come pre-installed on the device. This partition is mounted as read-only to avoid system malfunction. The system.img file is programmed into this partition.
-
cache: This partition is where Android stores frequently accessed data and application components.
-
vendor: This partitions contains the specific vendor files like binaries. This partition is mounted as read-only.
-
datafooter: Used by Android when device is encrypted. Once a device is encrypted, all user-created data is automatically encrypted before committing it to disk and all reads automatically decrypt data before returning it to the calling process.
-
safe: Empty placeholder partition for storing encrypted user-sensitive data.
-
frp: Factory Reset Protection. Security method designed to make sure someone can’t just wipe and factory reset your phone.
-
metadata: The metadata partition is used when device is encrypted.
-
userdata: Also called data, the userdata partition contains the user’s data – this is where your settings and applications are located. This partition is mounted as read-write. The SD Card folder is virtually emulated and mounted in this partition. This partition can be encrypted using a custom key.
-



