For the United States, cybersecurity is all about resilience. That’s why in July of 2023, the White House released its updated Cybersecurity Strategy with “A Path to Resilience.” The strategy aims to strengthen critical infrastructure, global cyberspace and U.S. intelligence against cyberattacks.
At a time when new technologies such as artificial intelligence and quantum computing offer both opportunities and threats, FIPS 140-2 has an important role to play in enhancing cybersecurity.
While this cybersecurity standard is employed by the U.S. and Canadian governments, anyone can adopt it. This article describes the purpose of this standard, as well as important use cases and recommend FIPS-validated products that can support your needs.
FIPS 140-2 Overview
FIPS stands for “Federal Information Processing Standards,” and 140-2 is the current version in place. The National Institute of Standards and Technology (NIST) developed the standard to help protect sensitive government information from hackers. FIPS 140-2 covers all cryptographic hardware, software and firmware that implements approved security functions.
In other words, for cryptographic modules to comply, they must integrate the features outlined in the standard. Therefore, if your cryptographic modules do not meet validation requirements, you cannot sell your solutions to the government. If you’re wondering what these requirements look like, here’s a brief overview.
FIPS 140-2 has 4 increasing security levels, which you can read about in our FIPS 140-2 Technical Brief.
Use Cases for the FIPS Cryptographic Standard
Ensuring that cryptographic modules (hardware and software) handling communications and data adhere to the FIPS 140-2 standard helps government agencies and government contractors alike conform to a standard framework for protecting data, operations, and assets against cyberthreats. In addition to the required government applications, other use cases include critical infrastructure, manufacturing, transportation and more. In the following section, we will dig into some use cases in government and beyond.
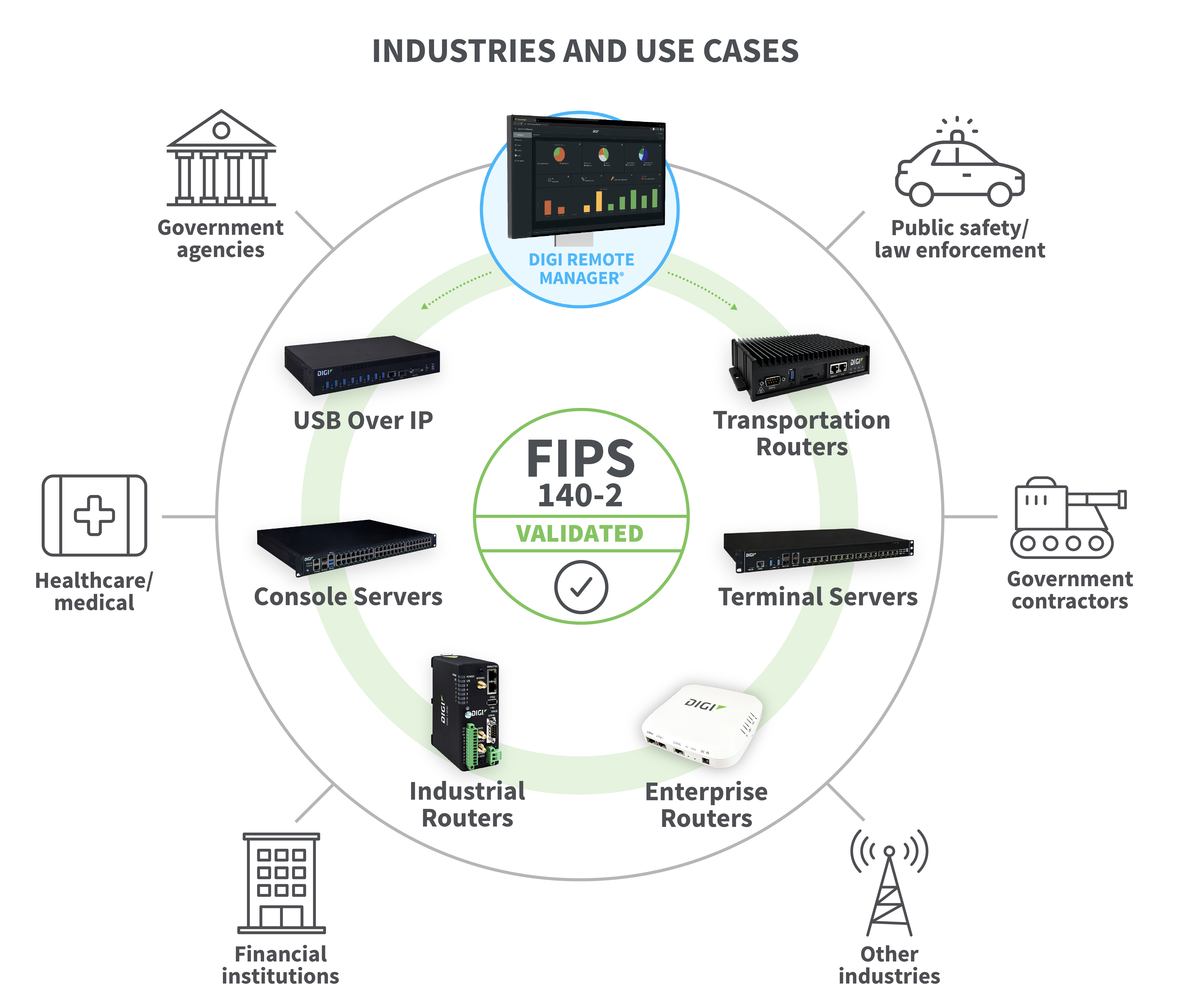
Applications Where FIPS 140-2 Validation Is Required
- Government agencies and contractors: The U.S. government represents one of the largest digital data consumers and producers. Data security is of paramount importance. For this reason, FIPS 140-2 validation is required for all entities handling Controlled Unclassified Information (CUI), which includes hundreds of government agencies, including the FBI, the Department of Defense, and U.S. Border Patrol, as well as all defense contractors and other services that contract with the government.
- Law enforcement: Law enforcement agencies utilize the Criminal Justice Information System (CJIS) which means they access highly sensitive information. For this reason police forces are required to use FIPS 140-2 validated devices. Additionally, they use devices like automated license plate readers (ALPRs) as part of their arsenal of in-vehicle technologies that transmit and share data. Compliance with the FIPS 140-2 standard ensures secure ALPR data during license plate data storage and transmission.
- Financial services: The financial industry is one of the most regulated industries in the world. Financial institutions that are part of the federal government, including the IRS and Federal Reserve, are required to use FIPS 140-2 validated devices to protect financial data from cyberthreats. Increasingly, other financial services and institutions are adopting the standard as well as a benchmark for cybersecurity.
- Medical institutions: Similar to financial institutions, those under government jurisdiction are required to use FIPS 140-2 validated devices. Additionally institutions that are required to be HIPAA compliant must follow the standard, and most healthcare institutions must be compliant for the protection of patient data. The risks are high. For example, Quest Diagnostics became a victim of cyber theft with over 12 million sensitive patient records stolen when attackers hacked a vendor payment web page. Compliance with FIPS 140-2 can help medical device manufacturers and healthcare software providers ensure that their encryption methods protect sensitive patient data and the security of medical devices patients’ lives depend upon.
Additional Applications Where FIPS 140-2 Compliance Is Beneficial
The benefits of FIPS 140-2 compliance cannot be understated, as every organization today must bolster its cybersecurity in the face of the increasing sophistication of hackers. FIPS 140-2 dramatically reduces the attack profile of organizations that handle everything from consumer data to financial transactions
- Manufacturing: Plasma Ruggedized Solutions manufactures conformal coatings, potting and encapsulation services specifically designed for FIPS approval. In other words, its products coat sensitive electronics to prevent access to data stored on treated printed circuit board assemblies. In fact, it even offers special measures to ensure that the product self-destructs if it detects further tampering such as unauthorized entry, modification, or reverse engineering.
- Energy and utility companies: Energy infrastructure, including gas, water and power utilities are central to everything we do. They’re critical for our economy and way of life. They’re also highly connected to thousands of endpoints that include power generation, energy providers and even smart meters. That’s why they need to be secured against increasingly sophisticated cyber-attacks. Beyond negative press and reputational damage, hackers can inflict financial damage and steal valuable intellectual property. For example, recent cyberattacks in the energy sector disabled remote controls for wind farms and led to data breaches of sensitive customer information. Preventing cyber threats means providing the highest levels of protection for all endpoints and data. Utilities that want to build resilience against cyberattacks can gain FIPS 140-2 validation on all encryption modules.
- Cloud data centers: Cloud services providers such as Google Cloud, IBM, AWS, Dell and Microsoft all use FIPS 140-2 validated encryption. This means that both data transmitted and stored data get encrypted using FIPS validated encryption.
- Unmanned vehicles: Unmanned vehicles range from unmanned aircraft such as drones to underwater unmanned vehicles and even self-driving cars. Because computer systems control virtually all unmanned vehicle operations, securing the data and information transferred remains a top priority. DJI, a drone and robotics company, sought FIPS 140-2 validation for some of its drones. According to DJI, all drones with the DJI Core Crypto Engine ensure that customers are “treated to trusted, authoritative, and globally recognized security standards.” Many DJI customers represent the federal government or work on government contracts, so it makes sense that DJI would seek FIPS validation for its products.
- Autonomous vehicles: As autonomous driving technologies improve, software-driven artificially intelligent vehicles will become more important to the future of mobility. These vehicles rely heavily on data and communication for safe operations, so cybersecurity remains a huge risk. The U.S. Department of Transportation’s 2022 pre-final report called Cybersecurity Best Practices for the Safety of Motor Vehicles cites FIPS 140-2 as a way to ensure that “cryptographic techniques should be current and non-obsolescent for the intended application.”
Work With a Trusted Solution Provider
 Although working within or as a vendor for the federal government means complying with FIPS 140-2 requirements, any organization that needs a robust level of cybersecurity protection can adopt the standard. That’s where Digi can help. Since 1985, Digi has been pioneering wireless communication. Today, Digi provides everything from sensor-based solutions and a sophisticated remote monitoring platform to full-service professional design, implementation and certification teams. When it comes to cybersecurity, we’ve got you covered.
Although working within or as a vendor for the federal government means complying with FIPS 140-2 requirements, any organization that needs a robust level of cybersecurity protection can adopt the standard. That’s where Digi can help. Since 1985, Digi has been pioneering wireless communication. Today, Digi provides everything from sensor-based solutions and a sophisticated remote monitoring platform to full-service professional design, implementation and certification teams. When it comes to cybersecurity, we’ve got you covered.
Digi solutions support FIPS 140–2 on the entire suite of devices based on the Digi Accelerated Linux operating system (DAL OS). See the full list on our FIPS 140-2 technology page.
Encryption is easy to implement. Digi Remote Manager, Digi's cloud-based solution for monitoring and managing devices, enables a simple process for keeping devices up-to-date. Simply upgrade your firmware and turn on FIPS. That’s it. Don’t get stuck with expensive and complicated solutions. Digi’s approach means your systems receive regular updates easily and at no extra cost.
Next Steps